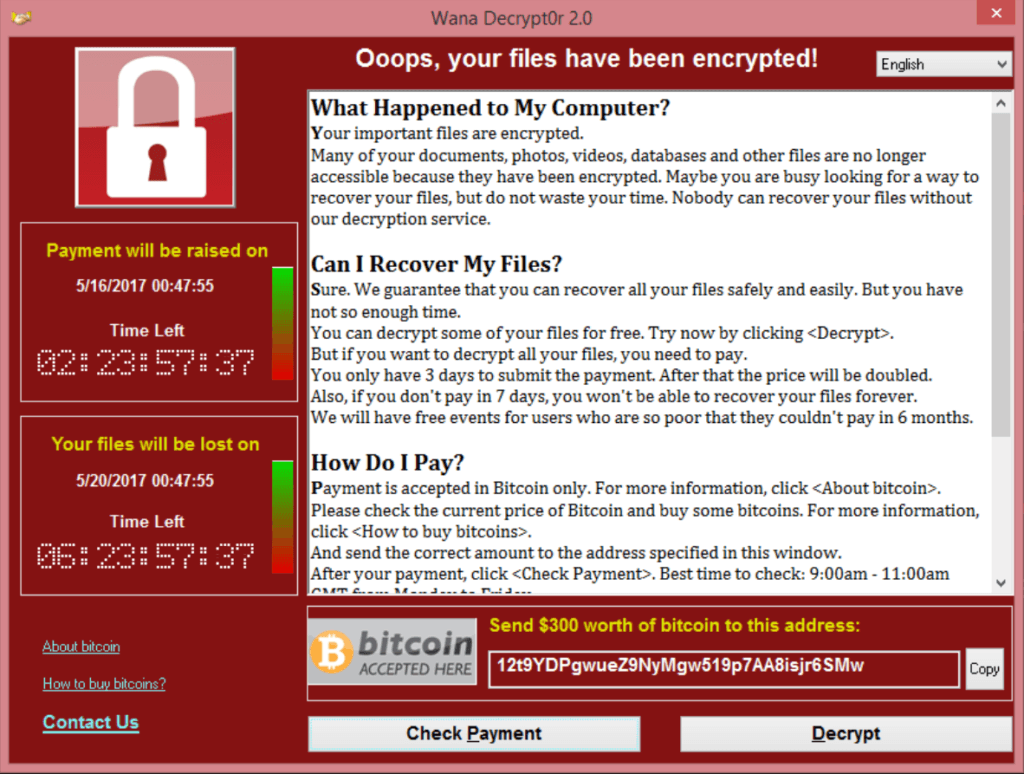
It makes you WannaCry
The rapid global spread of ransomware WannaCry at the end of last week should have made everyone think hard about security.
 Microsoft has angled its criticism at the security agencies for i) keeping vulnerabilities secret so that they can exploit them and ii) allowing them to be leaked and exploited by others. They pointed out that we might feel differently if it was Tomahawk missiles, but maybe we shouldn’t. It’s tempting to conclude that Microsoft got in first before others criticised them for failing to support older systems for long enough, and writing systems that had vulnerabilities in them in the first place.
Microsoft has angled its criticism at the security agencies for i) keeping vulnerabilities secret so that they can exploit them and ii) allowing them to be leaked and exploited by others. They pointed out that we might feel differently if it was Tomahawk missiles, but maybe we shouldn’t. It’s tempting to conclude that Microsoft got in first before others criticised them for failing to support older systems for long enough, and writing systems that had vulnerabilities in them in the first place.
Companies should also be subject to criticism for failing to apply patches quickly enough, and for using outdated software which was no longer supported. In fact they should probably be criticised for not taking security seriously enough overall.
i2O has taken a number of actions to up its security game, recognising that it serves an industry that is responsible for critical national infrastructure. i2O has:
- Appointed a Head of Security
- Implemented a Security Management System not as a tick-box exercise to get ISO 270001 accreditation but to ensure security is fully embedded into the business
- Started reporting monthly at Board level on breaches to security and actions to improve security in the same way as Health & Safety is reported
- Commissioned regular third party penetration testing and acts on findings
As a relatively slow adopter and refresher of software, the water industry has its fair share of old software. Anyone using it would immediately recognise the vernacular of Windows 95. In addition to its user interface being state of the art, there are a number of security advantages to our clients in using i2O's software service including:
- Separation of OT from IT (as advised by UK security agencies)
- We have responsibility for security and apply fixes and patches quickly with no client update/upgrade process
Instead of looking to blame other parties, each component of the supply chain would do well to think hard about what it can do to make things more secure. There’s an arms race in cyberwarfare and it pays to stay ahead.
Tags: Blog, LATAM, Europe, Africa, Security, UK, Asia Pacific, i2O, North America, Middle East