Could a botnet of loggers bring down a water utility?
The smart devices that make up the Internet of Things are proving very popular with malicious hackers. This is often because security wasn’t a key consideration for their manufacturers.
 Before the Internet of Things it was tricky to set up a network of hijacked devices. Most connected devices were computers and they, generally speaking, are relatively secure. The proliferation of connected devices – phones, cameras, printers, etc. – is multiplying the target base for the hackers.
Before the Internet of Things it was tricky to set up a network of hijacked devices. Most connected devices were computers and they, generally speaking, are relatively secure. The proliferation of connected devices – phones, cameras, printers, etc. – is multiplying the target base for the hackers.
A recent attack which took control of webcams and bombarded a switchboard for the internet Dyn, made access to popular websites, such as Reddit, Twitter, and Spotify difficult for a time.
But it’s not just domestic devices that offer hackers an opportunity. Machine-to-machine devices in the business world do too. There may not be as many of them, but the consequences of taking control of them could be much more serious.
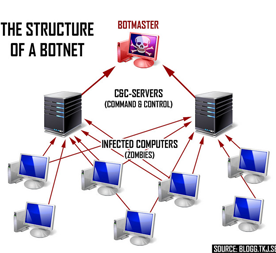
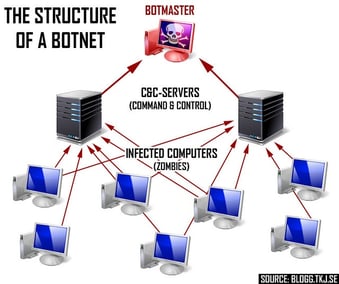
So, could a botnet of loggers bring down a water utility? Water utilities are increasingly deploying loggers to instrument their networks. Could these be used to bombard utilities with data and deny engineers timely access to the systems by which they operate critical national infrastructure? Yes, quite possibly. Too many logger manufacturers have not prioritised security in their design considerations. Anyone who could access the loggers could insert malicious code in them that increases the amount of data and frequency of transmission to produce a drowning attack on connected systems.
i2O has considered carefully the security of the solutions that it provides to the water industry. Here are a few ways we make our solutions secure.
- i2O loggers can’t be dialled up; they initiate contact with base. Most other loggers receive incoming calls. If you can dial them and make the right handshake, then you’re in.
- i2O’s latest loggers use military-grade encryption when communicating over the air.
- Software embedded in i2O loggers can be upgraded over the air. Chinese electronics firm Hangzhou Xiongmai issued a recall of its webcams soon after they were identified as aiding the recent DYN attacks. They had no other option because the software in the devices couldn’t be updated remotely. This enables a manufacturer to quickly address any security weakness that is exploited and prevent future attacks.
Hackers, like most wrongdoers, will leave difficult targets alone and exploit the vulnerable. i2O continues to work hard to ensure that its clients would be difficult targets, assuring the supply of clean water to their end customers.
Tags: Blog, Security, Asia Pacific, i2O, North America